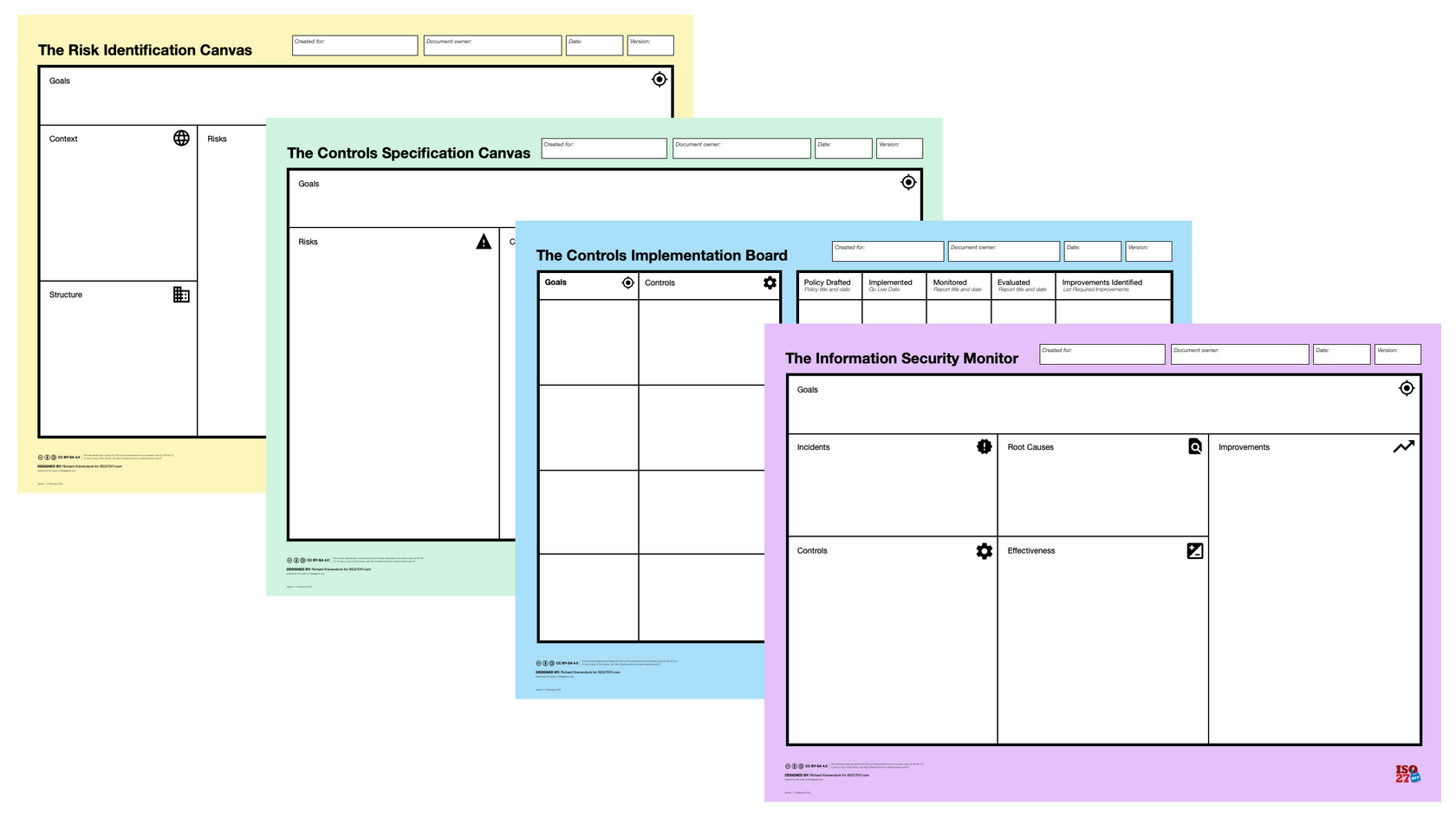
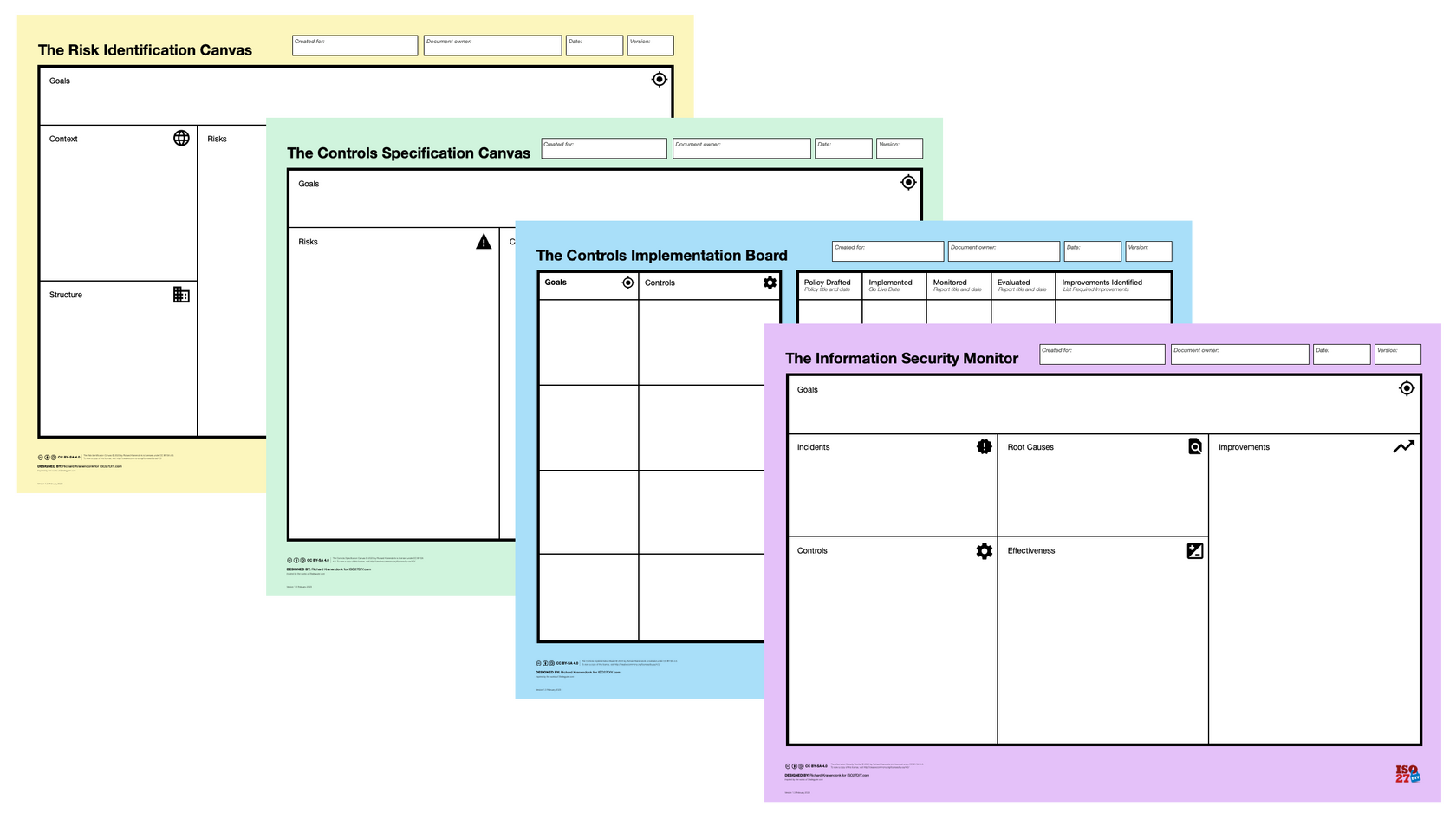
Create a Cybersecurity Culture
The Canvas Method for Information Security actively engages teams in risk identification and risk treatment.This heightens risk awareness and responsible behaviour throughout the organisation, and enables teams to make the right cybersecurity decisions.The Canvas Method helps internalise security policies and bridge the gap between compliance and business goals.
Get the Free Templates
We don't send spam and won't
share your data with anyone
Mastering Cybersecurity
The Canvas Method for Information Security will help you:
Establish risk awareness throughout the organization
Enable teams to make the right cybersecurity decisions
Create priorities based on actual risks
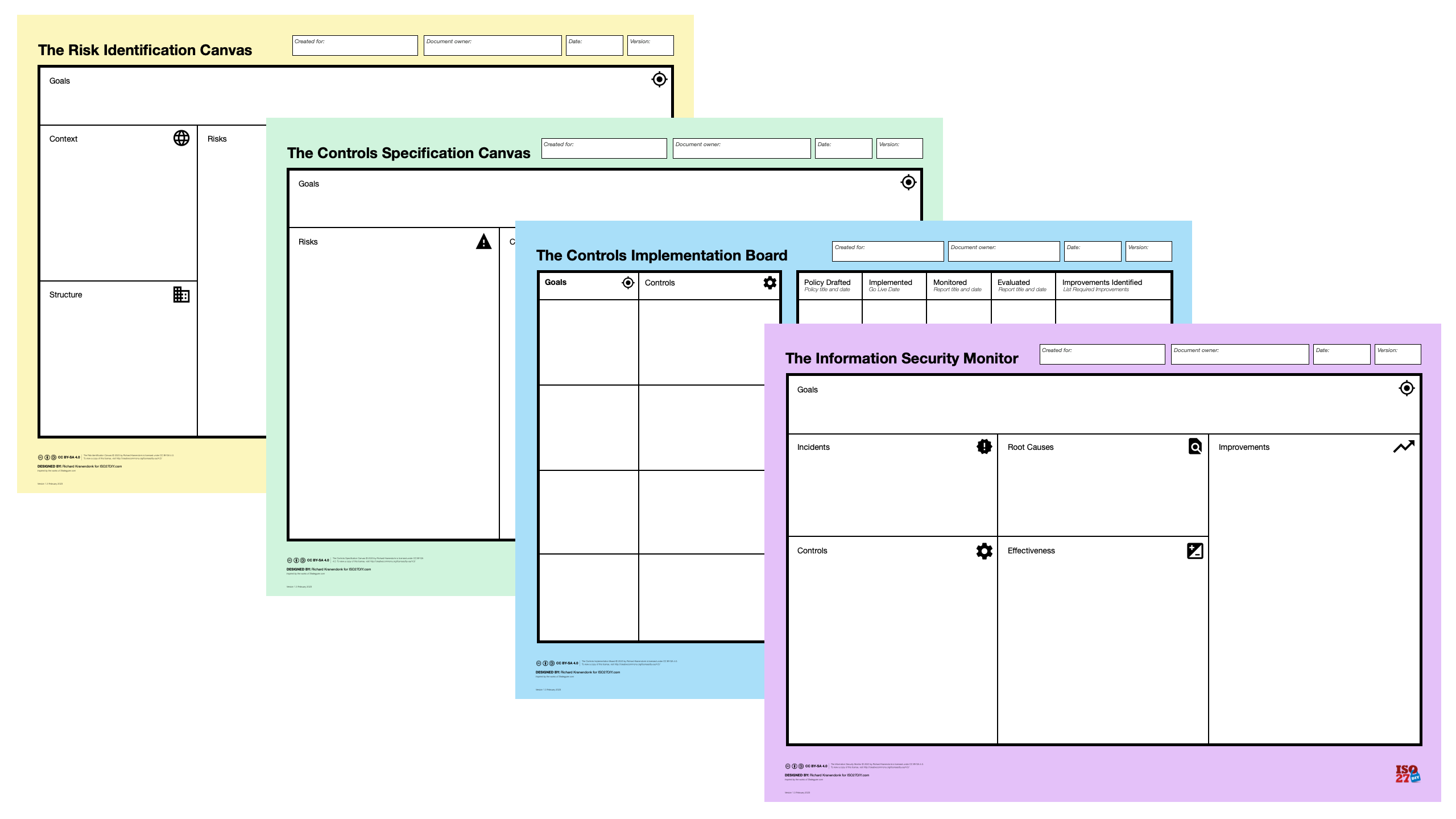
See the Canvas Method in Action
See how the Canvas Method establishes Information Security Management through a structured dialogue about risks and controls.
About the Canvas Method
The Canvas Method for Information Security was created by Richard Kranendonk as a tool for implementing a continuous and structured dialogue between business and security professionals.Richard studied organizational psychology in Amsterdam, worked in IT for 20 years, and now applies his knowledge and skills to bridge the gap between privacy and security frameworks and business goals.
Companies like Booking.com, Ultimaker, and Roche have used his services.

Do you want to learn how
the Canvas Method can
benefit your organization?
Canvas Method Workshops
Book a workshop for your team and learn how to implement the Canvas Method for Information Security in your own organization.

{1} Identify
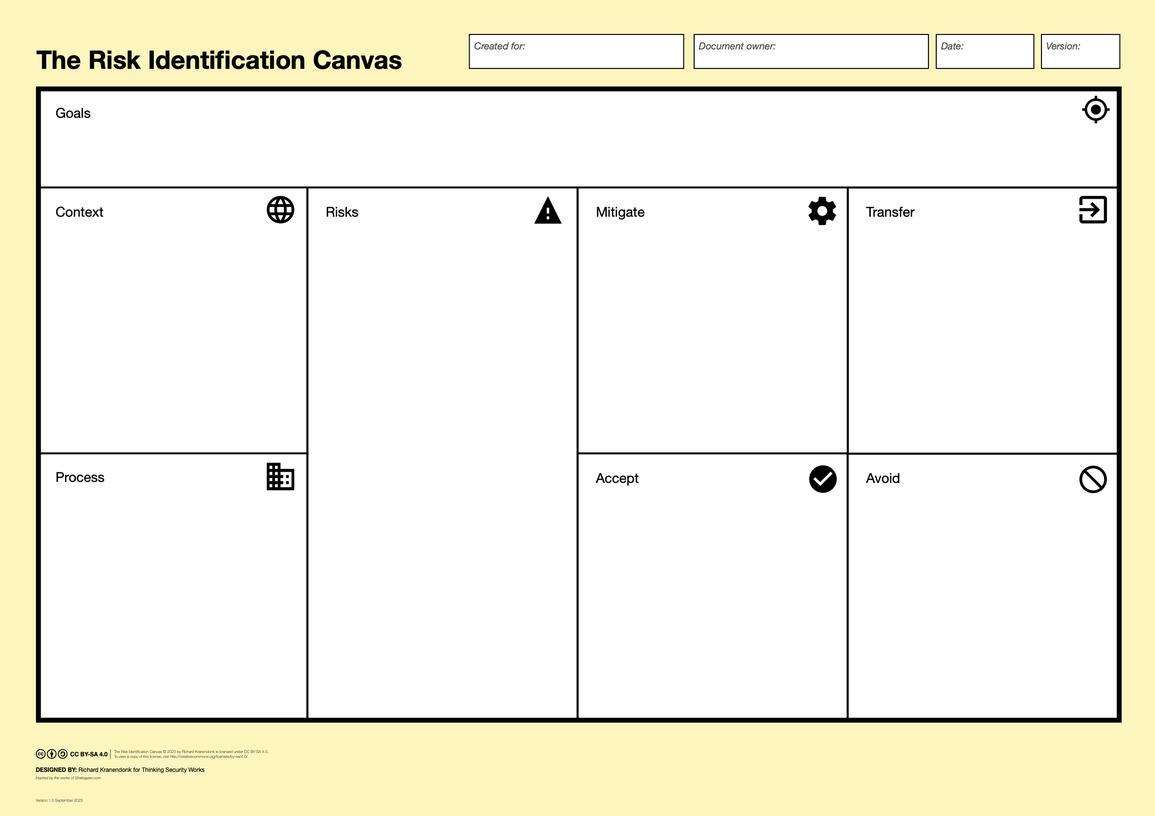
Use the Risk Identification Canvas to identify information security risks:
Identify risk sources in your team's context and work processes
Discuss information security risks arising from these sources
Decide on risk treatment
{2} Control
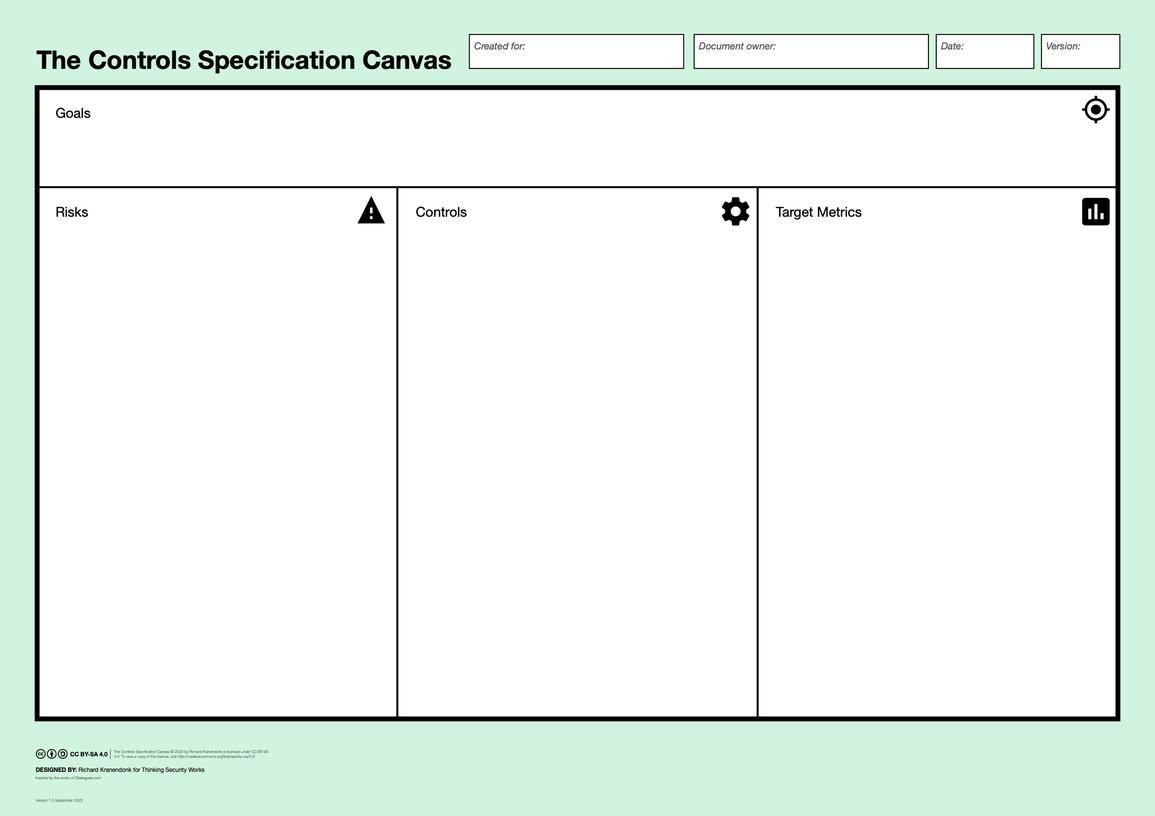
Use the Controls Specification Canvas to specify risk mitigating measures:
Specify controls to mitigate identified risks
Define methods and target values to establish control effectiveness
{3} Implement
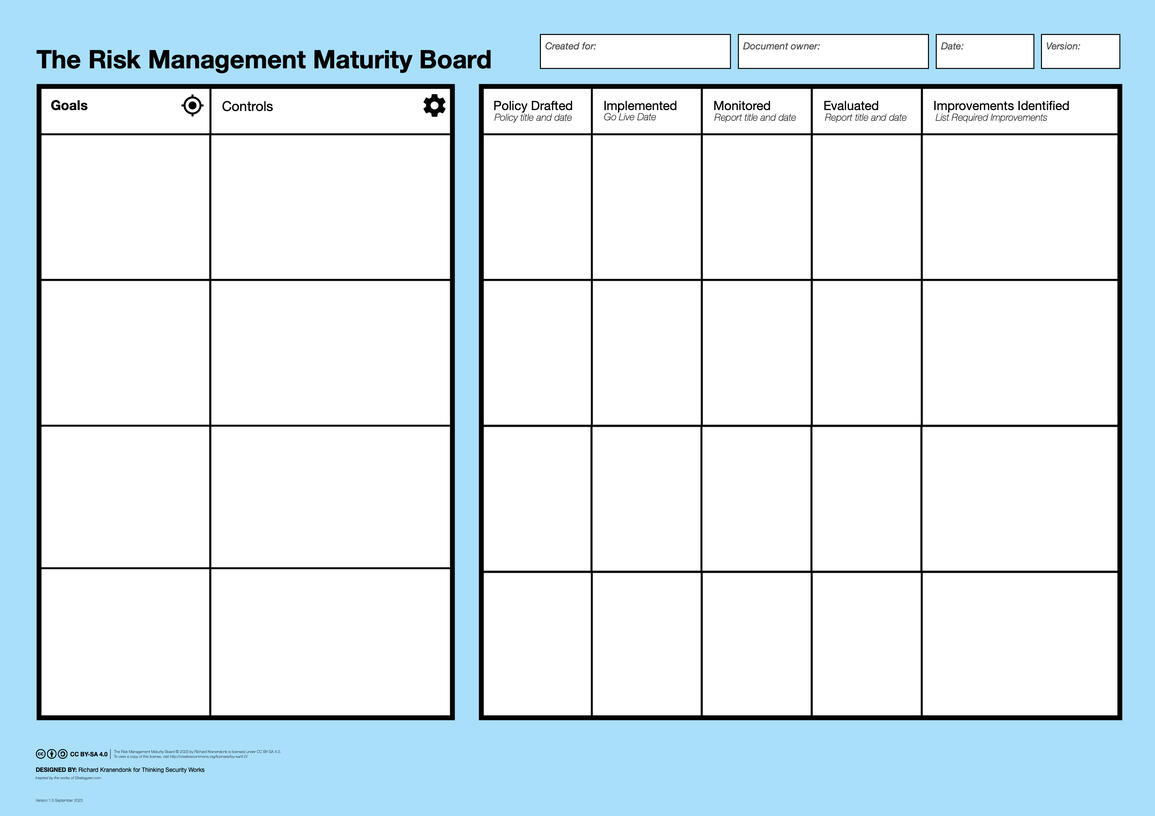
Use the Risk Management Maturity Board to implement an ISO 27001 compliant PDCA cycle for your security management:
Create a clear overview of security goals, and the controls to achieve them
Follow the implementation status for each control
Achieve continuous improvement
{4} Improve
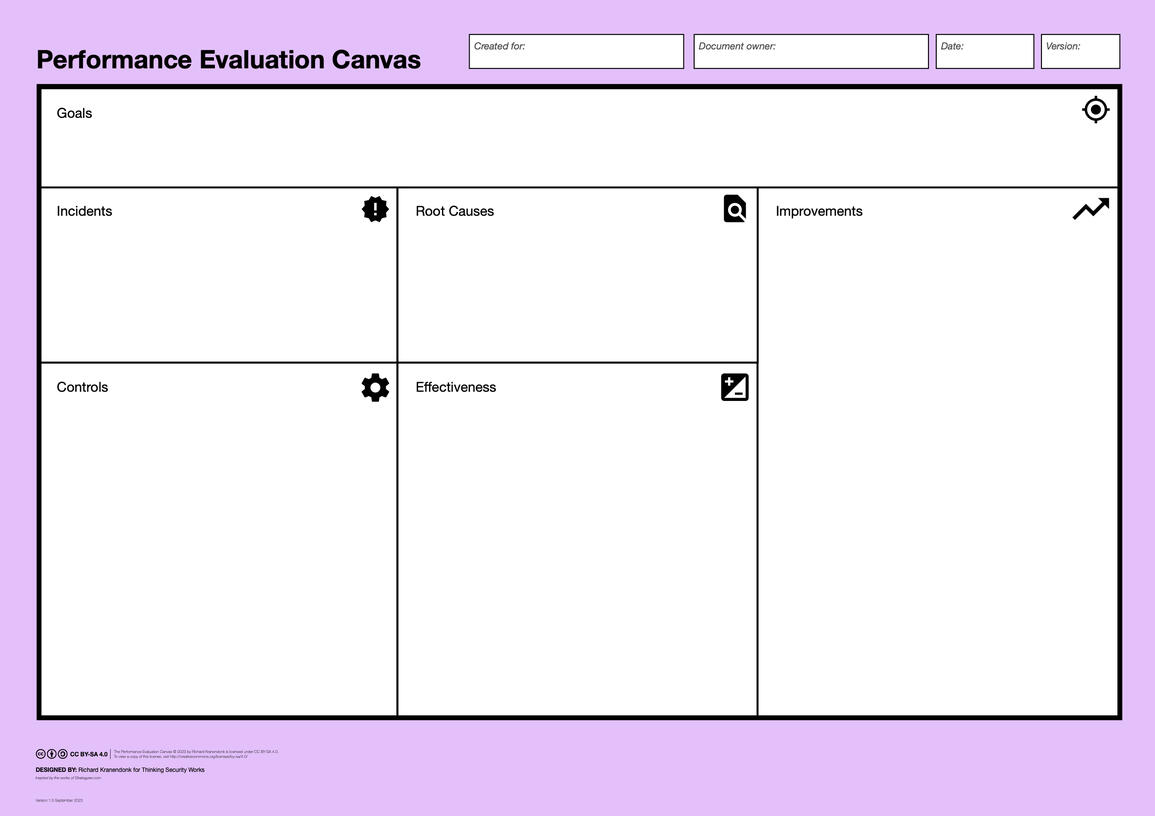
Use the Performance Evaluation Canvas to ensure the effectiveness and compliance of security controls:
Discuss recent incidents and their root causes
Identify additional controls to prevent future incidents
Report on effectiveness of controls
Set actions for further improvements
Canvas Method Workshops
In 2 online workshops of 2 hours each, we will take you through the Canvases as they apply to your own organization.
You will learn the basics of information security and risk management.
You will learn how to interactively identify and analyse risks, specify controls, create policies and define security metrics.
You will learn how to handle incidents and nonconformities, evaluate the effectiveness of your information security risk management, and identify improvements.
After the workshops, you will be able to implement the Canvas Method for Information Security in your own organization.
🚀 Launch offer for 2 workshops: €1495
Normal price is €1990
Thank you!
We will contact you promptly

Maak Informatieveiligheid onderdeel van je bedrijfscultuur
De Canvasmethode voor Informatieveiligheid betrekt teams actief in het identificeren en beheersbaar maken van risico’s.Dit verhoogt risicobewustzijn en bevordert verantwoordelijk gedrag in de organisatie. De methode helpt teams de juiste beslissing te nemen aangaande informatieveiligheid.De Canvasmethode zorgt voor internalisering van beleid en dicht de kloof tussen compliance en businessdoelen.
Download de Templates
We doen niet aan spam en zullen je gegevens met niemand delen.
Sturen op Informatieveiligheid
De Canvasmethode voor Informatieveiligheid zorgt voor:
Risicobewustzijn in de hele organisatie
Gefundeerde besluitvorming m.b.t. informatieveiligheid
Prioriteiten o.b.v. reeële risico's
Zien hoe de Canvasmethode wordt ingezet
Zie hoe de Canvasmethode sturing op informatieveiligheid implementeert, door een gestructureerde dialoog over risico's en maatregelen.
Over de Canvasmethode
De Canvasmethode voor Informatieveiligheid is ontwikkeld door Richard Kranendonk als instrument om een continue en gestructureerde dialoog te implementeren tussen bedrijfsonderdelen en security professionals.Richard studeerde psychologie aan de Universiteit van Amsterdam, heeft 20 jaar in de IT gewerkt, en zet sinds 2017 zijn kennis en kunde in om de kloof tussen privacy en security frameworks en bedrijfsdoelen te dichten.Organisaties als Booking.com, Ultimaker en Roche hebben van zijn diensten gebruik gemaakt.

Wil je weten welke voordelen
de Canvasmethode
jouw organisatie kan brengen?
Canvasmethode Workshops
Boek een workshop voor je team en leer hoe je de Canvasmethode binnen jouw organisatie kunt toepassen.

{1} Identificeren
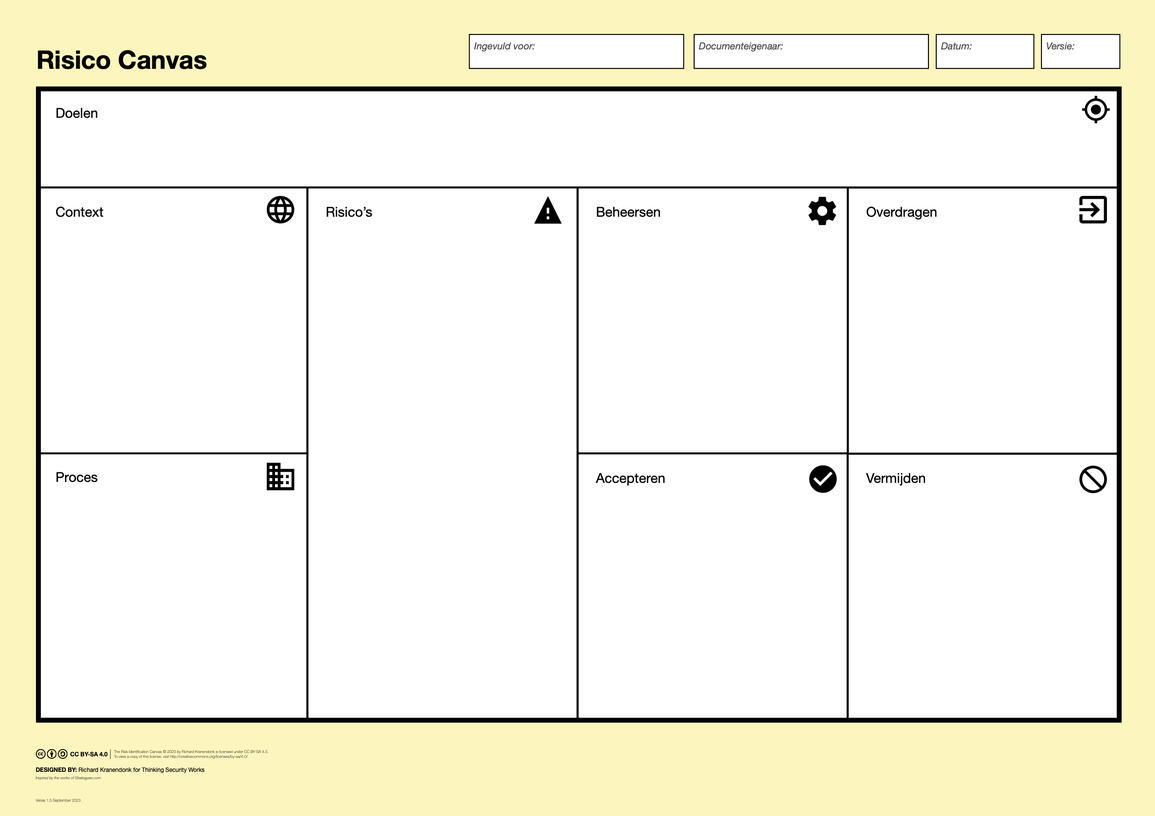
Gebruik het Risico Canvas om de informatieveiligheidsrisico's te bespreken:
Breng de omgeving en de processen van jouw team of afdeling in kaart
Identificeer potentiële risico's in context in proces
Bepaal risicobehandeling en eigenaarschap
{2} Beheersen
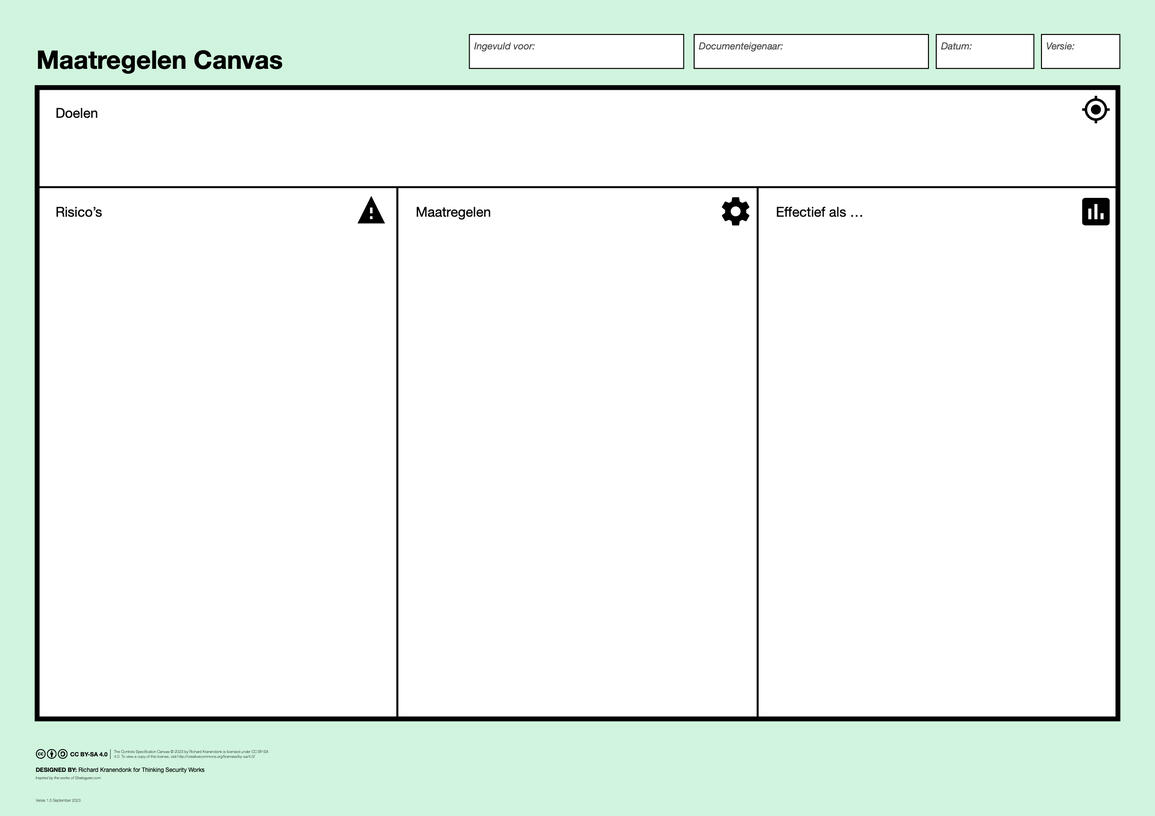
Gebruik het Maatregelen Canvas om risicobeperkende maatregelen te bespreken:
Specificeer maatregelen en beleid om de geïdentificeerde risico's te beheersen
Definieer meetmethodes en streefgetallen om de effectiviteit te bewaken
{3} Implementeren
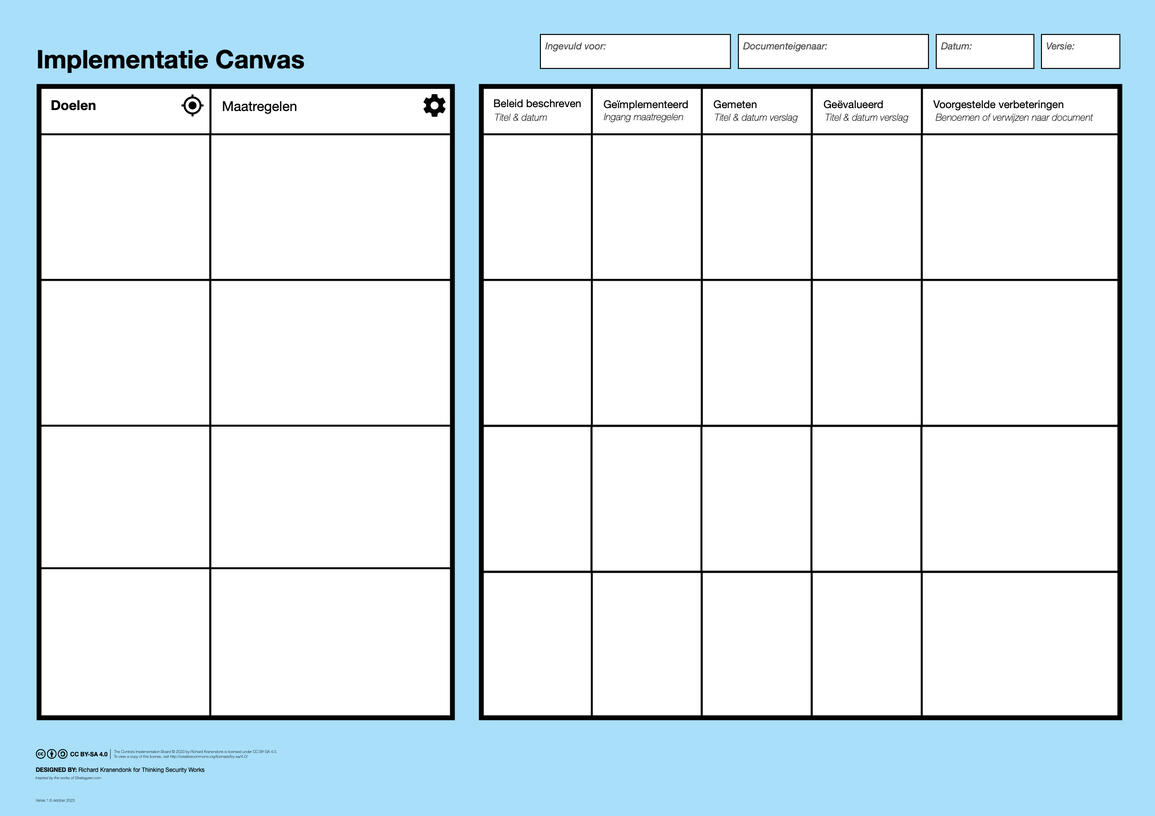
Gebruik het Implementatie Canvas om een PDCA cyclus te implementeren die compliant is aan ISO 27001 / NEN 7510:
Stel heldere doelen voor de informatieveiligheid van je organisatie
Beschrijf de belangrijkste maatregelen om die doelen te behalen
Volg de implementatiestatus van iedere maatregel
Bereik volwassenheid in je security management
{4} Verbeteren
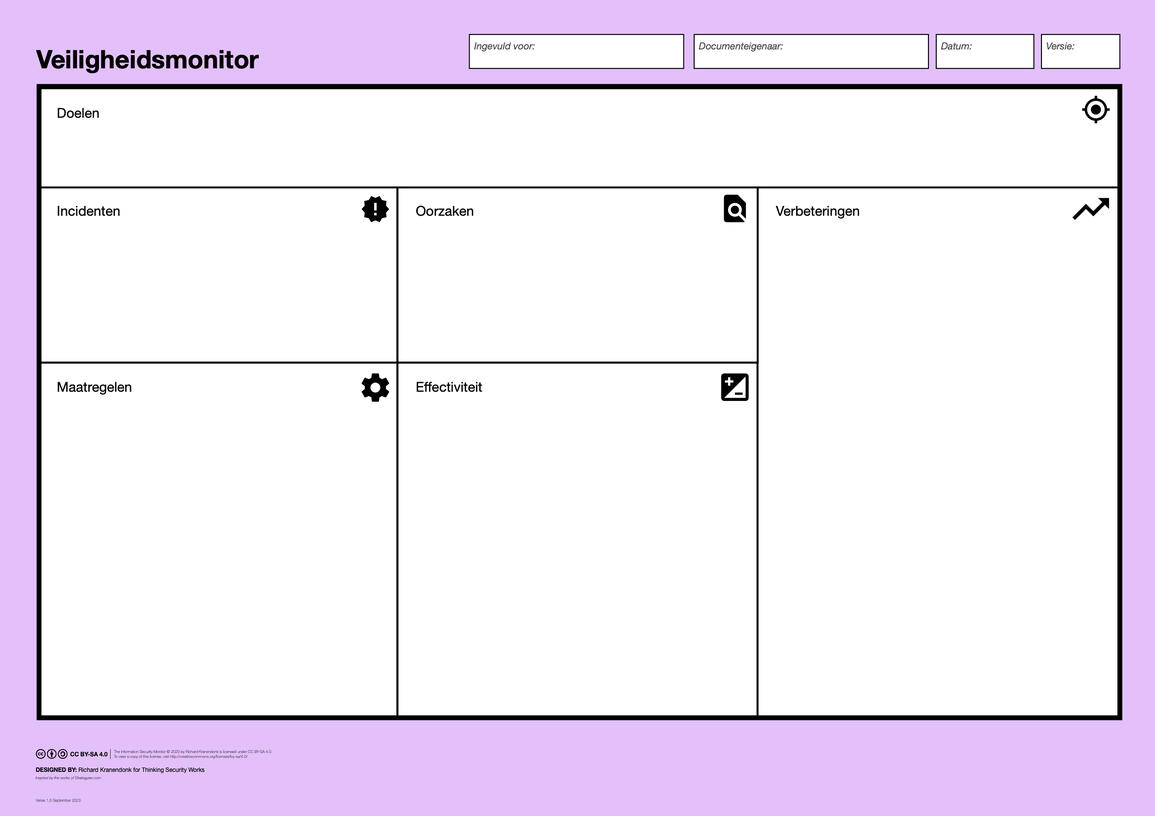
Gebruik de Veiligheidsmonitor om de effectiviteit van veiligheidsmaatregelen te bewaken:
Bespreek incidenten en hun oorzaken
Identificeer maatregelen om herhaling te voorkomen
Rapporteer over de effectiviteit van maatregelen
Bepaal acties voor verdere verbetering
Workshops Canvas Methode
In 2 online workshops van 2 uur nemen we je mee in het gebruik van de Canvassen voor jouw organisatie.
We leren je de essentie van informatiebeveiliging en risicomanagement
We leren je hoe je risico's interactief kunt identificeren en analyseren, maatregelen kunt bepalen, effectiviteit kunt meten, en beleid kunt opstellen.
Je leert incidenten en afwijkingen af te handelen, en hoe je de effectiviteit van je risicomanagement kunt verhogen.
Na het volgen van de workshops kun je de Canvas Methode voor Informatieveiligheid in je eigen organisatie toepassen.
🚀 Launch offer voor 2 workshops: €995
Normale investering is €1990
Dankjewel!
We nemen snel contact met je op